ISO 27001 2022 Package
2025-03-27 10:41ISO 27001 2022 Package
Get your certification at the lowest possible cost


ISO/IEC 27001 2022 complete package
2022 version



Price : 400 $
Certification Made Simple and Accessible for Your Business
The complete ISO/IEC 27001 2022 package is a comprehensive document package that contains everything from all the templates of procedures, processes, forms, checklists, tools, detailed guides and instructions needed to:
- Start your ISO/IEC 27001 process.
- Create your ISO/IEC 27001 documentation.
- Quickly access ISO/IEC 27001 accreditation.
- Benefit from an ISO/IEC 27001 management system that is simple and adapted to the needs of your organization.

Why start with a blank page. Start your Project TODAY, and save up to 80% on your time and money.

This package comes with 1 hour Live 1-to-1 Online Session with ISO consultant, document reviews, continual email support for 12 months and regular update service.

Cost-Effective Implementation: Much cheaper than an on-site consultant, and requires much less time than doing it from scratch
ISO/IEC 27001 2022 Version Complete Package
• Added Value: All ISO/IEC 27001 2022 requirements have been developed into an efficient process that adds operational value to your Laboratory and consequently increases productivity.
• Effective: Minimal effort is required to follow procedures necessary to meet all requirements of ISO/IEC 27001.
• Simplified: Bureaucracy and excessive paperwork have been eliminated from each process to make it easy – while remaining fully compliant with ISO/IEC 27001 2022.
Start your Project TODAY, and save up to 80% on your time and money.
The all-in-one document package for ISO/IEC 27001 2022 version
Save time, save money and simplify the accreditation process.
Documents included:

Procedures
- Procedure for identifying internal and external issues
- Stakeholder requirements identification process
- Procedure for defining and reviewing ISMS scope
- Information security policy development and review process
- Roles, responsibilities, and authority assignment procedure
- Procedure for management review
- Risk assessment methodology
- Risk treatment plan development process
- Planning and monitoring of ISMS objectives
- Process for addressing risks and opportunities
- Competence assessment and training procedure
- Awareness and communication management procedure
- Document and record control procedure
- Procedure for operational planning and control
- Information asset management procedure
- Risk assessment and risk treatment implementation procedure
- Incident response and management procedure
- Internal audit procedure
- Monitoring, measurement, and evaluation procedure
- Nonconformity and corrective action procedure
- Continual improvement process

Forms
- Register of internal and external issues
- Stakeholder needs and expectations register
- Roles and responsibilities matrix
- Management review meeting records
- Internal audit plan and checklist
- Audit findings and corrective actions log
- Records of ISMS-related communications
- Document control register
- Information asset inventory
- Records of operational activities and controls
- Incident response log
- Nonconformity and corrective action log
- Access Control Request Form
- Asset Inventory Record
- Change Request Form
- Cryptographic Key Management Record
- Incident Report Form
- Information Security Risk Register
- Internal Audit Report
- Management Review Minutes
- Monitoring and Measurement Results Record
- Nonconformance Report Form
- Risk Assessment Report
- Risk Treatment Plan
- Security Awareness Training Record
- Supplier Evaluation Record
- Vulnerability Scan Report

Quality Manual
- Documented ISMS Scope Statement
- ISO 27001 Information Security Management System (ISMS) Manual
- Information Security Policy

Plans
- Risk treatment plan
- Documented ISMS objectives
- Action plan to address risks and opportunities
- Competency matrix and training records
- Awareness and communication plan
- Monitoring and measurement reports
- Continual improvement plan and records
- Business Continuity Plan
- Disaster Recovery Plan
Others
- Information Security Risk Assessment Methodology
- Statement of Applicability (SoA)
- Information Security Objectives and Metrics

Access Control -Security Procedures
- Access Control Procedure
- Asset Management Procedure
- Change Management Procedure
- Communication Security Procedure
- Compliance Management Procedure
- Cryptographic Control Procedure
- Human Resources Security Procedure
- Information Security Continuity Procedure
- Information Security Objectives Procedure
- Information Transfer Procedure
- Operations Security Procedure
- Physical and Environmental Security Procedure
- Security in Supplier Relationships Procedure
- System Acquisition, Development, and Maintenance Procedure
- Technical Vulnerability Management Procedure
- Password Management Procedure
- Backup and Restore Procedure
- Patch Management Procedure
- Network Security Management Procedure
- User Access Management Procedure
- Mobile Device Management Procedure
- Data Classification and Handling Procedure
- Business Continuity Planning Procedure
- Disaster Recovery Planning Procedure
- Third-Party Security Management Procedure

ISO 27001 Documentation Requirements Explained
The ISO 27001 Documentation Package is a vital resource for organizations seeking to establish, implement, and maintain an effective Information Security Management System (ISMS). This comprehensive package includes all the necessary documentation to help your organization comply with ISO 27001:2022—the leading international standard for information security.
Comprehensive and well-structured documentation is essential for protecting sensitive information, managing risk, and ensuring regulatory compliance. From access controls to incident management, robust documentation supports a secure and resilient organization.
Why ISO 27001:2022 Documentation Matters
Proper documentation plays a critical role in safeguarding your organization’s information assets. It provides a structured framework for identifying threats, assessing vulnerabilities, implementing controls, and demonstrating compliance with international standards and client expectations.
This package includes:
Key ISO 27001:2022 Documentation Categories
| Document | Purpose in ISMS |
|---|---|
| Information Security Policy | Outlines the organization’s approach to managing information security |
| Risk Assessment and Treatment Plan | Identifies information security risks and defines treatment strategies |
| Statement of Applicability (SoA) | Specifies which Annex A controls are applicable and how they are implemented |
| Asset Inventory | Maintains a list of information assets and their classifications |
| Access Control Policies | Governs user access to systems and data |
| Incident Management Procedures | Defines how to detect, report, and respond to security incidents |
| Business Continuity Plans | Ensures the organization can recover from disruptions and continue operations |
| Training and Awareness Records | Demonstrates staff competence and awareness of security responsibilities |
Core ISO 27001:2022 Documentation Requirements
Management System Documentation
To comply with ISO 27001:2022, organizations must implement a risk-based management system focused on the confidentiality, integrity, and availability of information. Key documents include:
ISMS Manual – Describes the scope, objectives, and overall structure of the Information Security Management System.
Policies & Procedures – Provide clear guidance on how to manage access, handle data, and respond to incidents.
Risk Assessment Methodology – Defines how information security risks are identified, evaluated, and treated.
Statement of Applicability (SoA) – Aligns Annex A controls with actual practices and justifies exclusions.
Legal, Regulatory, and Contractual Requirements Register – Ensures compliance with applicable data protection and cybersecurity laws.
Operational Control Documentation
Strong operational controls are the backbone of a resilient ISMS. This package includes:
Access Control Procedures – Rules for granting, modifying, and revoking access rights.
Cryptographic Control Policies – Guidelines for encryption and secure data transmission.
Supplier Relationship Management – Defines controls for third-party access and data handling.
Backup and Recovery Plans – Ensures critical data is regularly backed up and recoverable.
Change Management Procedures – Controls changes to systems, software, and infrastructure that could affect security.
Monitoring, Evaluation, and Improvement Documentation
ISO 27001:2022 emphasizes ongoing performance monitoring and continual improvement. This package includes:
Internal Audit Plans and Reports – Evaluates ISMS effectiveness and identifies gaps.
Management Review Records – Provides leadership oversight and direction for ISMS performance.
Corrective and Preventive Action Reports – Addresses non-conformities and ensures long-term risk mitigation.
Monitoring and Logging Procedures – Tracks system activities and detects anomalies.
Performance Metrics and Objectives – Measures information security performance against established goals.
Legal and Administrative Documentation
Confidentiality and Non-Disclosure Agreements (NDAs) – Safeguard information shared with employees and third parties.
Information Security Roles and Responsibilities Matrix – Defines authority and accountability for ISMS tasks.
Awareness and Training Plans – Ensures personnel are equipped to uphold information security practices.
Document Control Procedures – Manages versioning, review, and approval of ISMS documents and records.
Ensure Compliance with ISO 27001:2022 Today!
Implementing an effective Information Security Management System can be complex, but with the ISO 27001 Documentation Package, your organization will have all the tools needed to secure data, build stakeholder trust, and meet certification requirements.
💡 Get started today and strengthen your information security posture with a structured, compliant, and future-ready ISMS!
90 Days Money Back Guarantee

If for whatever reason during the FIRST 90 days of your purchase, you are not satisfied for any reason, simply contact support@qse-academy.com and our support team will issue you an immediate and full refund.
The package includes all the documents you need to comply with ISO/IEC 27001 2022 – these documents are fully acceptable by the accreditation audit.
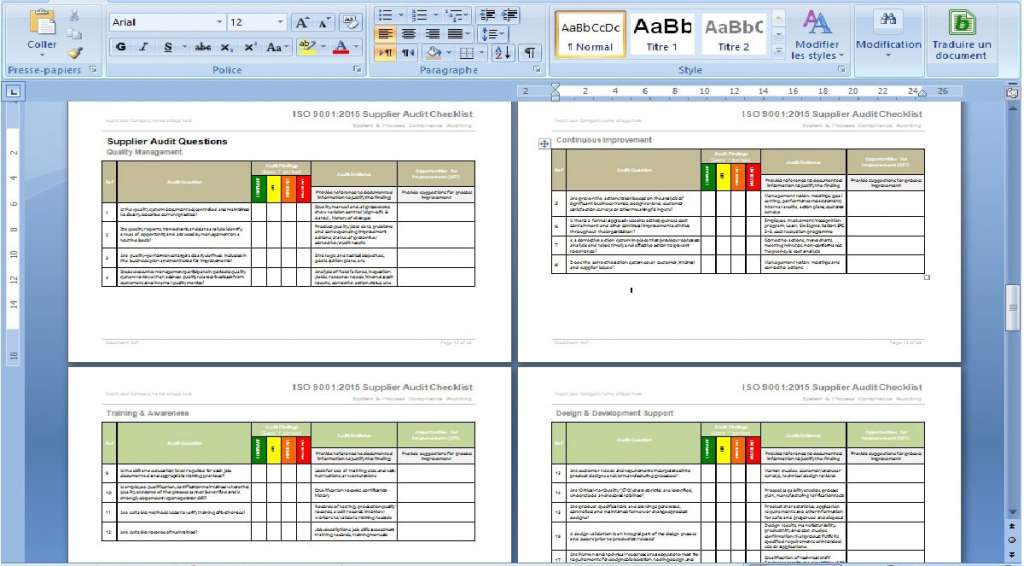
All documents are in MS Word or MS Excel, to make them very easy to customize for your business. You can customize them by adding company logos and colors, and edit headers and footers to match your favorite style.

We have already completed about 90% of the information requested on the documents. To complete them you must fill in only the name of the company, the responsible parties, and any other information unique to your company. you will be guided through the process, commenting on the elements that are needed and those that are optional.
We presented the ISO 27001 documentation, so as to assure all its users that they have completed everything accurately and with the utmost efficiency.

All the documents are made so that you can follow the proposed order perfectly, which allows you to make sure that nothing is missing, and that no one gets lost in the process.
The included comments and flowcharts help your staff understand each document and its usefulness, which helps you to make quality management more fluid, and processes easier to follow.
Features of the complete ISO/IEC 27001 2022 Kit
Price: 400 $
– Documentation included: 58 documents for the implementation of ISO 27001
– Language: English
– Documents are fully editable – just enter the information specific to your business.
– Acceptable for the ISO 27001 2022 certification audit? Yes, all the documents required by ISO 27001 2022 are included, as well as the quality policy and the current but optional procedures.
Instant Delivery – The package is downloadable immediately after purchase
Free Consultation – In addition, you can submit two complete documents for review by professionals.
Created for your business – The models are optimized for small and medium businesses.


Complete ISO/IEC 27001 2022 Package
The complete kit to implement ISO/IEC 27001
Price : 400 $
Total Implementation Duration: 8 Months
ISO/IEC 27001 Implementation Project Plan
Achieving ISO 27001 is a significant milestone for any organization, signifying a commitment to data protection and privacy. Our expert consultants are here to guide you through every step of the implementation process, from initial consultation and gap analysis to final assessment and compliance certification. With our comprehensive project plan, tailored training programs, and dedicated support, we ensure your organization meets all ISO 27001 requirements efficiently and effectively. Partner with us to enhance your organization’s credibility, improve data handling processes, and gain trust on an international scale. Let us help you achieve excellence in data privacy management.
Introduction: Project Kick-off and Gap Analysis (Duration: 1 Month)
Introductory Tasks
1.1 ISO 27001 Kick-off and Awareness
Task: Organize Kick-off Meeting
- Description: Conduct a kick-off meeting to introduce the ISO 27001 project to key stakeholders. Discuss objectives, timelines, scope, and responsibilities.
- Deliverables: Project plan, meeting agenda, and minutes.
- Meeting: Initial consultation with senior management and the ISMS team.
1.2 Perform Gap Analysis
Task: Conduct Gap Analysis Against ISO 27001:2022 Requirements
- Description: Assess the current information security practices and systems against the ISO 27001:2022 requirements to identify gaps and areas for improvement.
- Deliverables: Gap analysis report with identified non-conformities.
- Meeting: Present findings to senior management and the ISMS team.
Section 1: ISMS Scope and Risk Assessment (Duration: 2 Months)
2.1 Define ISMS Scope (ISO 27001 Clause 4.3)
Task: Define the Scope of the ISMS
- Description: Determine and document the scope of the ISMS based on business objectives, information assets, and the organization’s operational and regulatory requirements.
- Deliverables: ISMS scope document.
- Meeting: Review scope definition with senior management.
2.2 Conduct Risk Assessment (ISO 27001 Clause 6.1)
Task: Develop Risk Assessment Methodology
- Description: Define a risk assessment methodology to identify and evaluate information security risks related to assets, vulnerabilities, and threats.
- Deliverables: Risk assessment methodology and process.
- Meeting: Risk assessment review with the ISMS team and key stakeholders.
2.3 Perform Risk Assessment and Identify Controls
Task: Perform Risk Assessment and Identify Risk Treatment Options
- Description: Conduct a full risk assessment to identify risks to information assets and define appropriate controls (from Annex A) to mitigate or treat those risks.
- Deliverables: Risk assessment report and risk treatment plan.
- Meeting: Review risk assessment findings with senior management and key departments.
Section 2: ISMS Policy Development (Duration: 2 Months)
3.1 Develop ISMS Policy (ISO 27001 Clause 5.2)
Task: Define and Document the Information Security Policy
- Description: Develop the organization’s information security policy, aligned with ISO 27001 requirements, to define the overall commitment to protecting information assets.
- Deliverables: Information security policy document.
- Meeting: Review and approve the policy with senior management.
3.2 Establish Risk Treatment Plan (ISO 27001 Clause 6.1.3)
Task: Define and Implement Risk Treatment Plans
- Description: Based on the risk assessment, create risk treatment plans that specify the security controls and mitigation measures to address identified risks.
- Deliverables: Risk treatment plan and action items.
- Meeting: Review risk treatment plans with senior management and process owners.
Section 3: Implementation of Security Controls and Procedures (Duration: 1 Month)
4.1 Implement Security Controls (ISO 27001 Annex A)
Task: Implement Controls Based on Risk Treatment Plan
- Description: Implement the necessary information security controls (based on Annex A) across the organization, such as access control, encryption, and physical security measures.
- Deliverables: Security controls, configurations, and documentation.
- Meeting: Review control implementation progress with IT and security teams.
4.2 Develop and Implement Security Procedures
Task: Establish Procedures for Critical Security Areas
- Description: Develop procedures to support the implementation of controls, including incident management, change management, access control, and data backup procedures.
- Deliverables: Security procedures and work instructions.
- Meeting: Review procedures with IT, HR, and relevant departments.
Section 4: Awareness and Training (Duration: 1 Month)
5.1 Develop Security Awareness and Training Program (ISO 27001 Clause 7.2)
Task: Create Security Awareness and Training Plan
- Description: Develop a security awareness and training program to ensure that all employees are aware of information security risks and their responsibilities under the ISMS.
- Deliverables: Training plan, materials, and attendance records.
- Meeting: Conduct awareness sessions and workshops for employees.
5.2 Implement Ongoing Security Awareness Initiatives
Task: Launch Continuous Awareness Campaigns
- Description: Implement continuous awareness campaigns, such as email reminders, posters, and refresher courses, to maintain a high level of security awareness across the organization.
- Deliverables: Awareness materials and schedule.
- Meeting: Review the effectiveness of the awareness campaigns with management.
Section 5: Monitoring, Review, and Incident Management (Duration: 1 Month)
6.1 Develop Monitoring and Measurement Processes (ISO 27001 Clause 9.1)
Task: Establish Monitoring and Performance Measurement
- Description: Implement processes to monitor and measure the performance of the ISMS, including key security metrics and regular reporting on incidents, access violations, and control effectiveness.
- Deliverables: Monitoring reports and dashboards.
- Meeting: Monthly performance review meetings with the ISMS team.
6.2 Implement Incident Management Procedures (ISO 27001 Clause 6.1.3)
Task: Develop Incident Management Procedures
- Description: Establish procedures for identifying, reporting, and responding to information security incidents, including data breaches and system intrusions.
- Deliverables: Incident response plan, reporting templates.
- Meeting: Train staff on incident reporting and response procedures.
Section 6: Internal Audits and Corrective Actions (Duration: 1 Month)
7.1 Develop Internal Audit Program (ISO 27001 Clause 9.2)
Task: Create Internal Audit Plan
- Description: Establish an internal audit program to regularly assess the ISMS’s compliance with ISO 27001 requirements and identify areas for improvement.
- Deliverables: Internal audit plan, audit schedule, and checklist.
- Meeting: Review audit plan with internal auditors and ISMS managers.
7.2 Conduct Internal Audits
Task: Perform Internal Audits
- Description: Conduct internal audits to evaluate the effectiveness of the ISMS, security controls, and processes.
- Deliverables: Internal audit reports, non-conformance reports.
- Meeting: Review audit results with the ISMS team and management to identify corrective actions.
7.3 Implement Corrective Actions (ISO 27001 Clause 10.1)
Task: Develop and Implement Corrective Action Plans
- Description: Based on audit findings, develop and implement corrective action plans to address non-conformities and improve the ISMS.
- Deliverables: Corrective action plans, root cause analysis reports.
- Meeting: Review and approve corrective actions with senior management.
Final Assessment: Certification Preparation and External Audit (Duration: 1 Month)
8.1 Conduct Pre-Certification Internal Audit
Task: Perform Pre-Certification Internal Audit
- Description: Conduct a final internal audit to ensure that the ISMS meets ISO 27001:2022 requirements and is ready for the certification audit.
- Deliverables: Pre-certification audit report, corrective action plans.
- Meeting: Final review meeting with senior management and the ISMS team.
8.2 Certification Body Selection and External Audit
Task: Select Certification Body and Schedule Certification Audit
- Description: Research and select an accredited certification body for ISO 27001. Schedule the external audit and ensure the organization is fully prepared.
- Deliverables: Certification body selection report, external audit schedule.
- Meeting: Final meeting with management and the ISMS team to confirm readiness for certification.
This 8-month project plan for ISO 27001:2022 implementation ensures a structured approach to achieving certification for an information security management system. It covers key areas such as risk assessment, control implementation, incident management, internal audits, and certification preparation, aligning the organization with the ISO 27001 standard and ensuring the protection of information assets.
What our customers think:

QSE Academy’s ISO 27001:2022 package made implementation quick and cost-effective. The templates and guidance simplified the process, reducing consultant expenses and minimizing disruptions. We achieved accreditation faster than planned, saving nearly 50% of our budget. Highly recommended for an efficient ISO journey!
Morgan S.
IT Security Manager


“QSE Academy’s ISO 27001:2022 package helped us achieve certification quickly and affordably. The ready-to-use documents and clear guidance reduced our implementation time by 60%, saving us thousands without hiring consultants. The one-on-one support was invaluable. Highly recommended for a fast, budget-friendly solution!”
Emily T.
Operations Director

Frequently Asked Questions
How long will it take to receive the complete package of documents after I place my order?
Upon completing your purchase, you will be redirected to the download page immediately. Additionally, a link to access your file will be sent to your email. The files are provided in a .zip format, which you will need to extract. If you encounter any issues with the download, please do not hesitate to contact us at support@qse-academy.com. Our support team is always ready to assist you.
What payment methods can I use?
We offer several payment options for your convenience. You can choose to pay using a credit card, debit card, or PayPal. Additionally, we provide a flexible layaway plan for those who prefer to pay for their purchase over time. If you have any questions about our payment options, please don’t hesitate to contact us.
Do you offer a money-back guarantee if I'm not satisfied with the service?
We offer a 30-day money-back guarantee. If you are not satisfied with our service for any reason, you can cancel within the first 30 days and receive a full refund, no questions asked.
Is there ongoing support or assistance available after my purchase?
Yes! At QSE Academy, our ISO experts provide continued support by answering your queries via email. You can expect a detailed response within 24 to 48 hours to help you move forward confidently.
Are updates to the documentation package included after purchase?
Absolutely. To ensure your documentation remains reliable and compliant, we update our packages every 6 months. Existing customers receive these minor updates at no extra charge. However, when there’s a major revision of the ISO standard itself, you’ll need to purchase an updated kit to align with the new standard.
Will I receive a valid invoice for my business expenses after completing the purchase?
Yes. After completing your purchase, you’ll immediately receive a valid invoice suitable for business and tax purposes. If you require any specific adjustments or details added to your invoice, please reach out to our support team.
Can I customize these documents for my company's specific needs?
Yes, the documents are fully customizable! You can easily edit, modify, and add your company’s logo to tailor them specifically for your organization. Additionally, if you’d prefer assistance, we offer a personalized “Done-For-You” customization service to deliver audit-ready documents tailored exactly to your organization’s requirements.
How quickly can I implement this ISO standard using your documentation?
Implementation time varies depending on your company’s engagement, resources, and experience. Typically, we’ve observed businesses successfully achieve compliance and certification within 3 to 6 months using our clear, structured documentation packages.
Do these documents guarantee successful certification?
While our documentation packages significantly simplify the certification process, the ultimate success of ISO certification depends on effective implementation. For organizations seeking further assurance, we also provide comprehensive support services, including guided implementation and internal audits, to help you confidently pass your certification audit.
Do you offer hands-on assistance if I need extra help during implementation?
Definitely! If you prefer a complete, hands-off solution, we offer a premium “Done-For-You” implementation service. Our ISO experts handle the full preparation, providing you with audit-ready documentation and detailed implementation support. You simply adopt the customized materials, follow the tailored guidelines, and confidently pass your audit.






